Why Single Sign On (SSO) may not be enough
A single identity creates a web of relationships and access maps that can be exploited by hackers unless properly managed and understood.
Article by Brian Farrelly
Controlling the keys to your castle
In today’s interconnected digital world, the convenience of using a single identity across various platforms is tempting. I recently had some work done in my house where all doors were set up as ‘key alike’, so one key rules them all. Convenient, totally. Secure? I’m not so sure. I’ve got kids, and when they have keys, the security of my home is no longer in my hands alone! A single identity (or key!) creates a web of relationships and access maps that can be exploited by hackers unless properly managed and understood.
If a hacker has one key that fits all the locks, it’s game over very quickly. This blog post explores why having separate identities and passwords, along with non-linked systems, can be inherently more secure in appropriate circumstances, and how tools like password managers and multiple MFA platforms can enhance your security. Using multiple identities and passwords across different platforms enhances security by creating multiple barriers, reduced ‘blast radius’ and reducing the risk of lateral movement within your environment. How we secure our identities, in particular with regards to MFA, is critical not only to protecting your business but speaks to compliance requirements and industry regulatory needs that need to be satisfied.
The Problem with a Single Identity
Using a single identity across multiple platforms means that if one account is compromised, all linked accounts are at risk. Hackers can easily trace the relationships between your accounts, gaining access to sensitive information and potentially causing widespread damage. This interconnectedness creates a single point of failure, making it easier for cybercriminals to infiltrate your digital life.
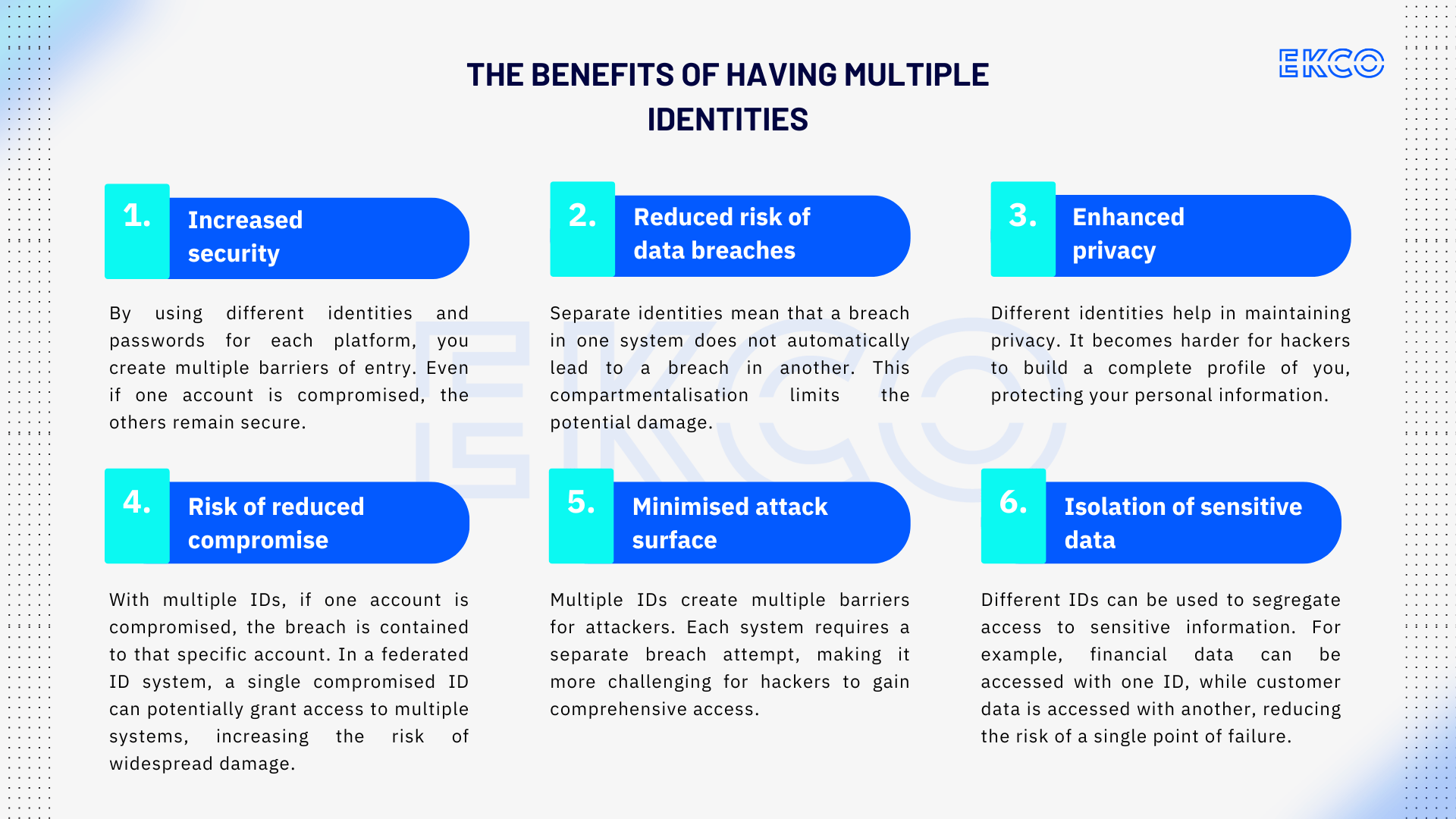
The benefits of having multiple identities
- Increased security: By using different identities and passwords for each platform, you create multiple barriers of entry. Even if one account is compromised, the others remain secure.
- Reduced risk of data breaches: Separate identities mean that a breach in one system does not automatically lead to a breach in another. This compartmentalisation limits the potential damage.
- Enhanced privacy: Different identities help in maintaining privacy. It becomes harder for hackers to build a complete profile of you, protecting your personal information.
- Reduced risk of compromise: With multiple IDs, if one account is compromised, the breach is contained to that specific account. In a federated ID system, a single compromised ID can potentially grant access to multiple systems, increasing the risk of widespread damage.
- Minimised attack surface: Multiple IDs create multiple barriers for attackers. Each system requires a separate breach attempt, making it more challenging for hackers to gain comprehensive access.
- Isolation of sensitive data: Different IDs can be used to segregate access to sensitive information. For example, financial data can be accessed with one ID, while customer data is accessed with another, reducing the risk of a single point of failure.
Non-linked systems further enhance security by ensuring that even if one system is compromised, it does not provide access to others. This approach involves using unique passwords for each account, ensuring they are strong and not reused across different platforms. Employing MFA adds an extra layer of security, making it harder for hackers to gain access even if they have your password. Additionally, regularly updating passwords helps reduce the risk of long-term exposure whether you are using a single federated identity or isolated account. Interestingly Microsoft have some amazing stats showing that most (not all!) of Azure hacks are on accounts with no MFA, and they are addressing with the requirement for Admin MFA for portal access coming into force in October 2024.
Password managers are invaluable tools in maintaining multiple identities and strong, unique passwords. They generate complex passwords that are difficult to crack, store them securely, and simplify password management by allowing you to remember just one master password. This makes it easier to manage multiple accounts, and we here at Ekco recommend the Keeper Security platform to meet these needs. Multi-Factor Authentication (MFA) adds an additional layer of security by requiring more than one form of verification. Using multiple MFA platforms can further enhance security by offering diverse verification methods such as SMS codes, authentication apps, and biometric verification. Even if one MFA method is compromised, the others provide additional layers of protection.
Operational flexibility is another advantage. Granular access control allows for more precise control over who has access to what, which is particularly useful in large organisations where different departments or roles require different levels of access. Tailored security policies can be applied to different IDs based on the sensitivity of the data they access, with more stringent authentication methods for critical systems. Additionally, having multiple IDs makes it easier to track and monitor access and activities, helping to quickly identify and respond to suspicious activities.
Sometimes a bunch of keys is better than one
While the convenience of a single identity is known, it should only be used in the appropriate scenarios with the correct security controls. Adopting multiple identities, unique passwords, and non-linked systems, you create a robust defence against cyber threats. Utilising tools like password managers and multiple MFA platforms further enhances your security. Remember, in the digital world, security needs to be balanced with convenience.
At Ekco, we understand these challenges and can help you make the best decisions and strategies around your identity landscape. Reach out to our team today to discuss your requirements.

Question?
Our specialists have the answer



